Legal regulations in most countries allow shareholders meetings, annual general meetings and the work of management and supervisory boards to take place without the need for a physical meeting. The legislator allows for online voting.
A secret ballot cannot be guaranteed by a notary.
A secret ballot cannot be guaranteed by a notary public, because having information about the voting method of a specific person, he would not be able to disclose it due to the obligation of secrecy. It is also necessary to meet the other legal requirements related to voting in the traditional form (e.g. adequate notification of the meeting, delivery of a written version of resolutions, etc.).So how do you conduct an online secret voting?
Electronic voting is confidential when none of the voting persons will know how the other voted. It is recommended to use the so-called trusted third party - recipient of votes. Usually a suitable secret voting application is required. Sometimes, the numbers of resolutions and responses by the chairman are manually encoded (encrypted). The vote of each participant is transferred in a coded form in order to calculate the final result of the vote by the recipient of the votes. For example, a resolution with the number 1 is marked as "#", with the number "2", eg "&" etc. However, a vote for, for example, "r", and against as "5" (differently for each vote). Therefore, the recipient of votes does not know how individual participants voted, and their task is only to calculate the voting results in a coded form. Then the chairman of the meeting decodes them according to a known key and announces the results.However, the manual coding solution has several disadvantages:
How do commercial companies deal with remote voting?
Most companies simply don't hold remote meetings, especially online secret voting. Unfortunately, this generates costs for the physical presence of voters due to their geographical spread, and sometimes it is impossible to vote due to pandemic constraints.Many entities use solutions that do not meet the requirements set out in the acts, exposing themselves to the risk of appealing against the adopted resolutions.
There are often use:
- existing survey solutions
- forms created in popular videoconferencing tools
- not fully adapted solutions from different vendors, usually transformed from voting systems in local government units
| Threat description | Solution in the privote system |
| Integrity | |
| Usually a videoconference system and a voting system are two non-integrated systems. This causes the lack of credibility, for example, of the voting video identification, because it is not certain whether the person seen in the image transmission is the same person who voted. For the same reason, there are doubts about the correctness of the calculation of the required quorum. The sum of the votes cast may not constitute the basis for determining the quorum. The voter has the right to be present and not to vote. | The videoconferencing system is fully integrated with the voting system. In fact, the video communication system has been expanded to include voting functions. One login and complete consistency of video, voice, recording and votes. When voting starts, the quorum is checked and an attendance list is created (for this voting). |
| Security | |
| Even leading solutions send passwords to users in an open form, unencrypted e-mails, and access to video transmission is protected only by a link and PIN code shared by everyone. This creates a risk not only of unauthorised access to the meeting, but also of an unauthorised voting. | A user of the privote system receives a link with an invitation to register. He independently defines his password and accepts all documents required by law (personal data processing policy, confirmation of exclusive access to the e-mail address and telephone number, and, if the voting person so wishes, a document created by the voting entity - e.g. voting rules). The connection is encrypted with an SSL certificate, and the latest technical solutions used (including HTML5 and WebRTC) guarantee the security and confidentiality of the transferred data. |
| Data consistency and immutability | |
| Voting forms created in one of the popular videoconferencing programs do not offer any guarantee of reliability and correctness. They can be modified at any time and no one can guarantee that they will be tested competently. Some of the suppliers even boast of the possibility of changing the documents attached to the meeting at any time, and even the possibility of changing voting parameters after its commencement or completion! | privote .net sp. z oo is fully responsible for the correctness of voting results, which (upon request) confirms with its qualified digital seal. Modification of meeting and voting parameters is blocked at the moment of its commencement. It is only possible to add new votes if additional motions are submitted during the meeting or if it is necessary to reassess the vote. |
| Functionality for complex votes | |
| There is often no way to define more complex votes. For example, qualified majority 2/3 with quorum 3/4 excluding certain voters (e.g. during voting in matters of discharge for the Management Board). | The system is prepared for all types of voting (open, secret, simple, absolute, qualified majority, quorum and voter exclusion). |
| Verification of secret ballots by voters | |
| It is not a formal requirement, but such functionality increases the comfort and confidence of voters, ensuring that the secret vote is properly qualified. | privote is the only solution that allows the voter to verify his secret vote without violating the secrecy of the vote itself. This is possible thanks to our proprietary Smart Vote ID technology - during the patent protection procedure. |
The choice of the solution used for online voting is important not only in terms of the efficiency and speed of the meeting. One should also take into account the risk of appealing against the resolutions to the court by the shareholders dissatisfied with the decision.
A wrongly selected voting program and improperly conducted, e.g. a remote general meeting of shareholders or any remote meeting (of the management board, supervisory board, etc.) provides an unnecessary excuse for disputes about the validity of resolutions.
Online secret voting can already be carried out using the services of the appropriate provider. We encourage you to use the privote system or to verify other solutions, paying attention to the aspects listed in the table above.
If it is so good, why is it so bad? How to vote remotely?
Often in the press or television there are reports that an organization (e.g. a political party) or company cannot adopt some resolutions because they concern personal matters and it is not possible to vote by secret online voting. Such reports seem strange because there are already appropriate legal regulations allowing for this type of voting. There are also technical solutions and applications for secret voting.
So what's the problem?
It seems that the problem results from the reluctance to this type of voting and some mental resistance and lack of trust, which is important precisely in the case of secret voting in remote mode.
It is easier to understand this mechanism when we look at the infographic below.
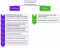
As you can see, the difference between traditional secret voting and online secret voting is huge. There are considerable disproportions in the ability to control its proper course.
In the traditional version, voters see all stages and can make sure that the entire process is correct.
In the online version, they have to trust that the whole process has gone smoothly and that the results are real.
Modern cryptography has long enabled such transfer of information to ensure its secrecy. It is also possible to check whether a vote has been qualified to the correct pool.
The problem is that the mechanisms and algorithms that enable online secret voting are understood by only a handful of engineers, cryptologists, and mathematicians.
Well, cryptology, artificial intelligence and block chain technologies will do nothing if it is not convincing for the average recipient, who will be able to independently control the correctness of casting a vote, as it is in the case of traditional voting.
This deficiency in online technology causes mental resistance and distrust of voters in remote voting systems.
Many business managers simply don't know how to vote online in a safe and reliable way. Online voting platforms are new to the market of tools for commercial law entities and there is a lack of reliable ratings and opinions.
Is it possible to solve the problem of verifying the vote cast in the case of secret online voting?
There is a fairly widespread belief that there is no technology that will provide both secrecy, verifiability and simplicity understandable by the average voter.It seems to be true in the case of general elections.
Here, the scale of voting is enormous and the risk of potential abuse is significant. Even securing the votes with an SMS code is quite easy to circumvent. If we already solve all technical problems and ensure secrecy and verifiability, then at the very end there will be ordinary human actions, such as the fact that access to voting is given to an unauthorized person.
The media reported on such cases in parliaments of various countries.
Note that the traditional form of elections is protected by many security features, such as voting recording, election commission, shop stewards, external independent observers, etc. Even the transmission of ready-made voting protocols via the Internet poses a risk of manipulation. However, in the case of remote meetings and voting in commercial law entities, social, political or local government organizations, it is possible to solve the problem of verifying the secret vote cast by means of electronic communication.
One such solution is SVID (Smart Vote ID), the proprietary privote technology (pending patent protection).
It enables simple, understandable for an average user and reliable online verification of a secret voice without violating the secrecy of the voting itself.
An additional element enabling the elimination of the mistrust of voters in online voting systems is the fundamental difference in the legal definition of the secrecy of these votes.
In the case of commercial law entities, secret voting means secrecy only to voting participants.
In other words, it is permissible to manage voting by an external entity, i.e. the so-called a trusted third party or recipient of the vote. This is the function of privote.net LTD.
Many entities and organizations disregard this requirement, commissioning their IT departments to prepare online voting with the use of free or unadapted tools.
These systems are usually not tested and verified in any formal way, and the fact that they are prepared by an employee of the company violates the principle of an independent recipient of votes.






